4 Healthcare Cybersecurity Challenges

Tables of Contents
Digital technologies make it easier and more efficient to deliver patient care and provide better outcomes. However, the rise of digital technologies and the growing interconnectedness between different healthcare systems come with increasing healthcare cybersecurity threats.
The benefits of healthcare technology advancement are undeniable. Electronic health records (EHRs) have become critical to improving diagnostics and patient outcomes, with 75% of healthcare providers reporting that EHRs help them deliver better patient care, according to HealthIT.gov.
With providers increasingly relying on technological advancements, healthcare cybersecurity threats have risen in tandem. The cybersecurity firm Emsisoft reports that the U.S. had more than 560 cyberattacks against healthcare facilities in 2020.
What can healthcare organizations do to address the challenges? Strategies include the following:
- Implementing cybersecurity technology
- Building a talent pool of professionals skilled in healthcare cybersecurity
- Developing a healthcare cybersecurity strategy focused on patient privacy protection
- Addressing vulnerabilities in legacy systems in healthcare
- Keeping tabs of new developments to understand information technology (IT) challenges
These steps can bolster an organization’s cybersecurity defenses, minimize security breaches in healthcare, and help ensure that critical systems remain operational to minimize the impact to patient care.
Issues faced in healthcare cybersecurity
Healthcare cybersecurity is an area of information technology focused on protecting healthcare systems. These systems include EHRs, health tracking devices, medical equipment, and software used for healthcare delivery and management. Healthcare cybersecurity focuses on preventing attacks by defending systems from unauthorized access, use, and disclosure of patient data. The primary aim is to ensure the availability, confidentiality, and integrity of critical patient data, which, if compromised, could put patient lives at risk.
Hospitals house hundreds and even thousands of patients, making them prime targets for hackers and making healthcare cybersecurity an important area of concern for hospital leaders. A 2018 attack on the Hancock Regional Hospital in Greenfield, Indiana, shows how a ransomware attack can impact cybersecurity in hospitals. Hackers accessed backup system data and permanently corrupted files, including EHRs. The hospital remained operational even after the IT team shut down the network, so thankfully, patients didn’t have to be diverted. However, the attack did impact the hospital financially — it wound up paying a ransom of four bitcoins valued at $55,000 to get its data back.
Cyberattacks come in many forms, from ransomware to theft of personal information. The impact of an attack can vary depending on the size of the facility. Four issues are common throughout healthcare: patient privacy protection, the vulnerabilities of legacy systems in healthcare, the challenges of IT in healthcare, and security breaches in healthcare.
#1: Patient privacy protection
As the healthcare industry becomes more technologically connected, the risk of cyber theft also increases. The two types of theft are outside theft and insider misuse.
- Outside theft: Hackers from a location outside of a healthcare organization penetrate patient and medical systems to steal and collect data, mainly for financial gain. For example, they might use patients’ personal information to submit fraudulent claims to health insurers. According to the Office of Inspector General, medical identity theft disrupts care and wastes taxpayer money. Outside theft can also include hackers forcing healthcare organizations to pay a ransom in return for restoring patient data systems. In 2020, healthcare data breaches from external actors exceeded inside breaches — 51% and 48%, respectively — according to Verizon.
- Insider misuse: Insider misuse often comes in the form of theft of patient data for financial gain or malicious intent. Other types of insider misuse include curiosity (unwarranted access to data not related to delivery of care) and convenience (overriding security protocols to make a job easier). Unintentional actions such as human error, including mistyping information into EHRs or clicking on a phishing email, make up the rest of insider misuse cases.
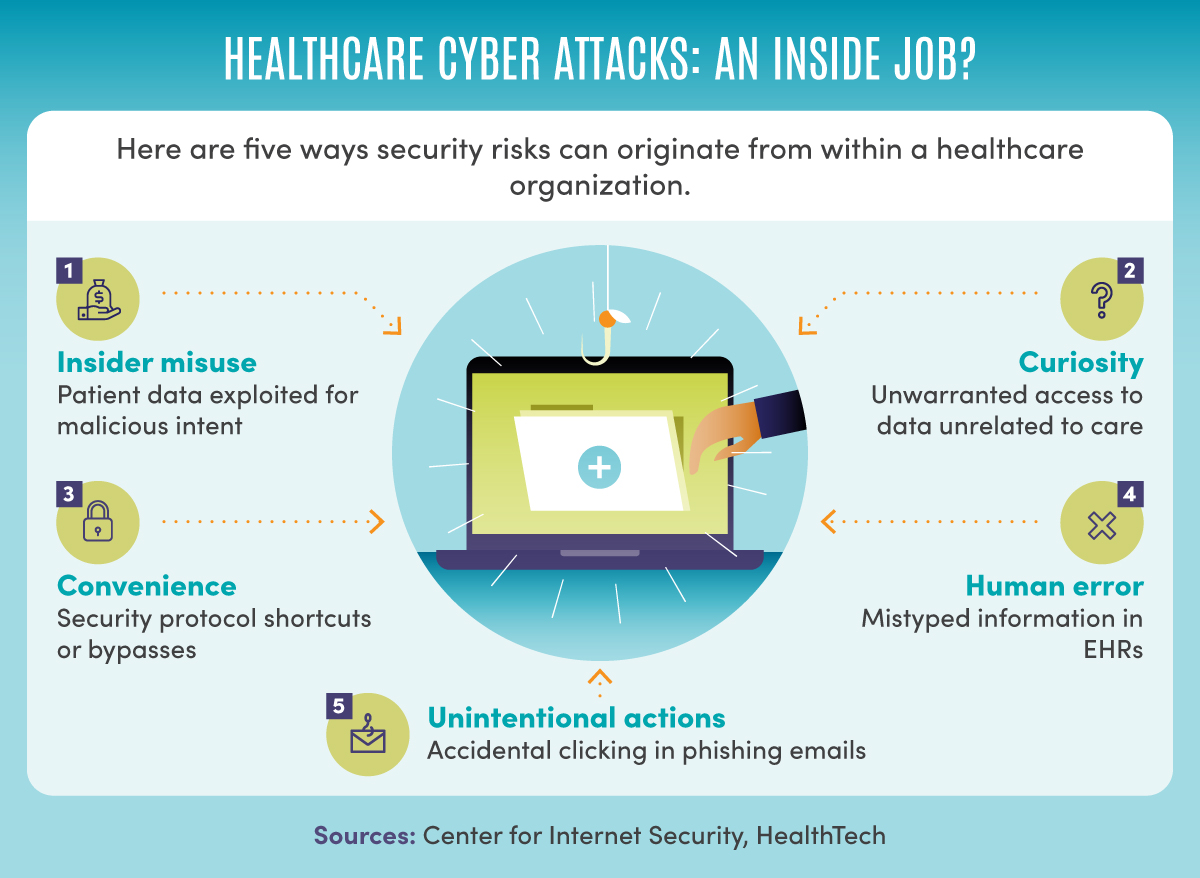
Here are five ways security risks can originate from within a healthcare organization, according to the Center for Internet Security and HealthTech: insider misuse, where patient data is exploited for malicious intent; curiosity, or unwarranted access to data unrelated to care; convenience, or security protocol shortcuts or bypasses; human error, such as mistyped information in EHRs; and unintentional actions, such as accidental clicking in phishing emails.
With the Health Insurance Portability and Accountability Act (HIPAA) of 1996, healthcare organizations are legally obligated to protect patient privacy. The HIPAA Privacy Rule sets limits on how patient health information is used and shared with other healthcare practitioners. Through cybersecurity measures and by adhering closely to legal regulations and standards, healthcare organizations can help ensure that patient data is kept away from potential cybercriminals.
Patient privacy informational resources
The following links provide additional information about patient privacy laws, such as HIPAA regulations, and resources available for patients and healthcare providers:
- AAFP, AAFP Advocacy Focus: Patient Privacy (HIPAA): Information and links to other resources related to HIPAA in family medicine.
- Healthcare.gov, For Individuals: Answers to common questions about patient privacy.
- HealthIT.gov, Health Information Privacy Law and Policy: An overview of patient choice, opt-in policies, patient consent laws, and more.
- HHS.gov, Department of Health and Human Services, The HIPAA Privacy Rule: A definition and history of the Privacy Rule.
- Rural Health Information Hub, Patient Privacy: How the Privacy Rule applies to rural health c
#2: Vulnerabilities of legacy systems in healthcare
Replacing legacy systems with up-to-date digital tools can maximize health outcomes and provide healthcare providers, administrators, IT staff, and patients with better experiences. It can also minimize vulnerabilities. However, change is difficult. Before undertaking a transition, an organization should outline a strategy with input from multiple stakeholders. A considered plan can result in a successful transition if healthcare organizations are willing to take on challenges.
Despite the benefits digitization provides, many healthcare systems keep outdated legacy systems for the following reasons:
- Tight budgets to perform upgrades: Moving to a new system includes the costs of buying new technology and paying technicians. It may also mean downtime, which reduces opportunities for a healthcare facility to generate revenue.
- Compliance guarantee: Compliance processes to certify new equipment and technology can be tedious. Organizations that have already gone through the process once may prefer not to undertake it again.
- Upskilling costs: Training staff on new systems is time-consuming and costly, but necessary to minimize errors. Together with training from technology vendors, programs such as the American Hospital Association Team Training program can help leaders integrate teamwork principles into new healthcare systems.
- Complacency: Healthcare organizations may opt to fix a problem only after a system failure or hack — after the damage is done. A proactive approach to replacing legacy systems can help avoid future problems.
A common characteristic of legacy systems in healthcare is their vulnerability to cyberattacks — providing “back-door entry” for cybercriminals to access systems that hold personal and medical data. In addition to the danger to patients, data theft can interrupt workflows, impacting staff performance. Another factor that increases the vulnerability of legacy systems is the lack of support from third-party vendors. Once a technology is outdated, it becomes increasingly difficult to find the necessary support to address issues or fix problems.
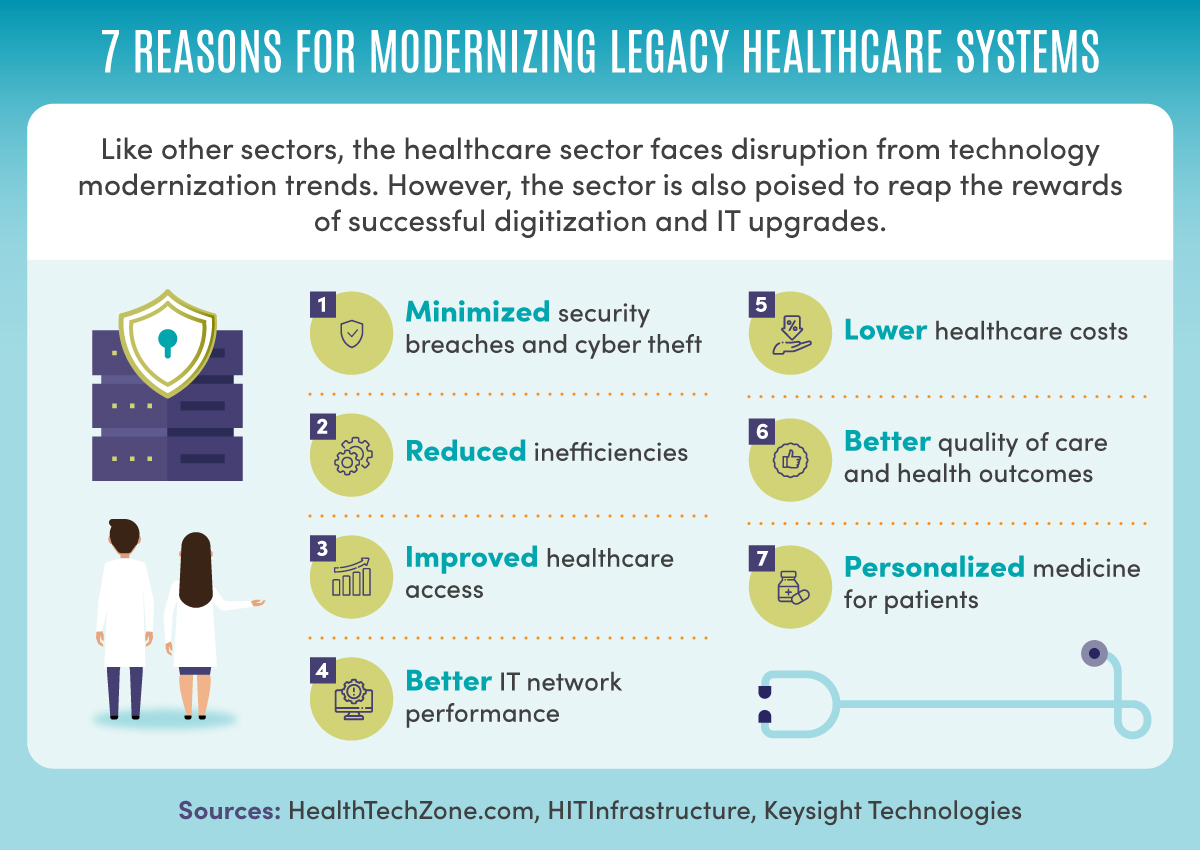
Like other sectors, the healthcare sector faces disruption from technology modernization trends. However, the sector is also poised to reap the rewards of successful digitization and IT upgrades, according to HealthTechZone.com, HITInfrastructure, and Keysight Technologies. Seven reasons for modernizing healthcare legacy systems include minimized security breaches and cyber theft; reduced inefficiencies; improved healthcare access; better IT network performance; lower healthcare costs; better quality of care and health outcomes; and personalized medicine for patients.
#3: Challenges of IT in healthcare
The increased use of IT in healthcare has provided benefits such as better communication between doctors and patients, automation of manual tasks, and improved communication between physicians caring for the same patients. IT and digitization have also empowered patients to make better decisions about their care, as patients have greater access to information about their health through EHRs and patient portals.
Additional benefits of IT and digitization in healthcare include the following:
- Reducing inefficiencies
- Improving healthcare access
- Lowering healthcare costs
- Enhancing care quality
- Providing more personalized medicine for patients
To achieve the benefits, connected technologies are essential, although they are also targets for cyberattacks and data breaches. Despite external breaches surpassing internal misuse as the predominant source of security risk, internal misuse is more common in the healthcare industry compared with other industries, according to Verizon.
For IT leaders trying to minimize security breaches in healthcare, reduce cyber theft, and increase patient privacy, strengthening cybersecurity remains a high priority. According to a LexisNexis Risk Solutions Group white paper, improving cybersecurity is the second most important focus among healthcare chief information officers.
Another key challenge for IT in healthcare is managing interoperability, which is cited as the first priority among technical leaders in healthcare in the LexisNexis white paper. Managing interoperability deals with how to effectively close gaps in information shared across different digital points of contact. Healthcare leaders look to address the challenges by transforming business and healthcare processes to align with digitization trends and improve performance.
Resources: IT opportunities in healthcare
The following resources discuss how technology offers the healthcare industry opportunities to improve performance in relation to reducing security risks, improving delivery of care, and optimizing health outcomes:
- Agency for Healthcare Research and Quality, Health Information Technology Integration: Resources for integrating health information technology into primary care.
- Healthcare IT News, “Technology Optimization: Enriching Healthcare Communications”: Experts’ best practices for optimizing healthcare systems to improve outcomes.
- HealthTech, “3 Methods for Minimizing Security Risks in Healthcare”: The case for protecting the weakest links and education to reduce the impact of healthcare cybersecurity threats.
#4: Security breaches in healthcare
In 2020, the healthcare industry saw hackers taking advantage of COVID-19 fears. One example involved an email about a supposed “coronavirus map” to track COVID-19 cases; clicking on the link activated information stealer malware that stole passwords and credit card information.
Some of the biggest healthcare data breaches of 2020 came from fraud schemes, phishing attacks, and vulnerabilities in healthcare vendor systems. For example, HealthITSecurity reports that more than 1 million patients were impacted when hackers breached a third-party system from Dental Care Alliance, with 10% of patients’ bank account numbers breached.
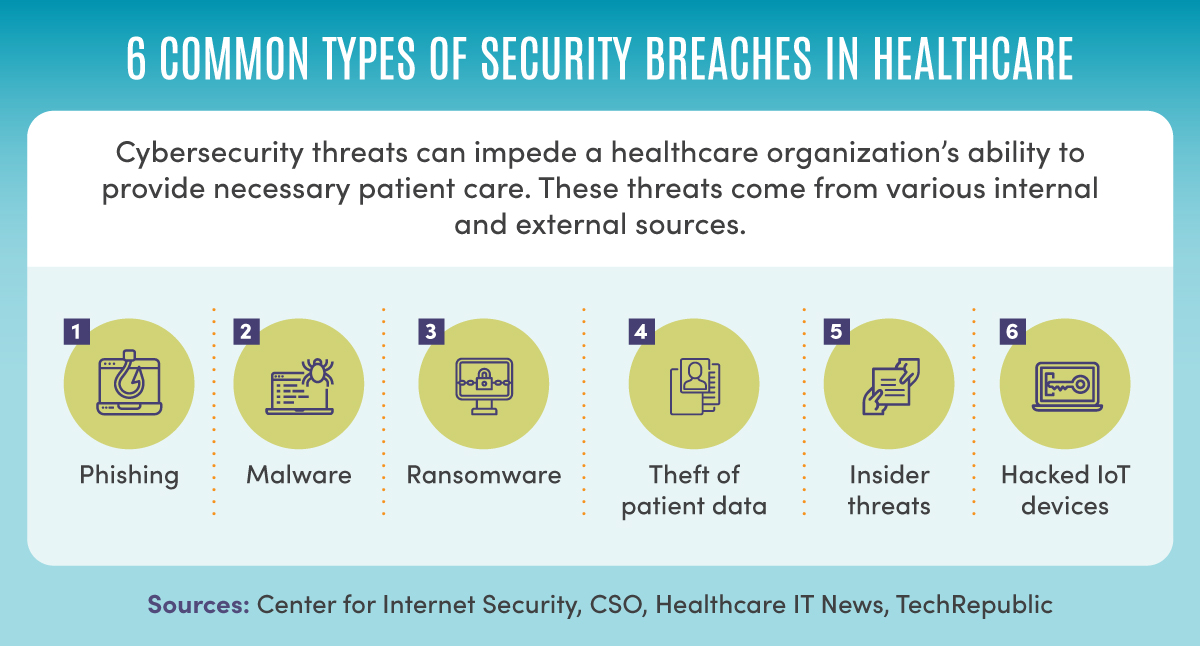
Cybersecurity threats can impede a healthcare organization’s ability to provide necessary patient care. These threats come from various internal and external sources, according to the Center for Internet Security, CSO, Healthcare IT News, and TechRepublic. Six common types of security breaches in healthcare include phishing, malware, ransomware, theft of patient data, insider threats, and hacked IoT devices.
Phishing, malware, ransomware, theft of patient data, insider threats, and hacked Internet of Things (IoT) devices — these are just a few concerns of healthcare cybersecurity professionals.
- Phishing: A hacker impersonates a trustworthy email source to entice users to click on a link. Through this means, hackers can obtain personal information, such as credit card numbers and passwords.
- Malware: Software created to cause damage to a computer, a network, or another connected system. Malicious software can come in the form of a virus, a Trojan horse, spyware, and adware.
- Ransomware: A type of malware that uses encryption to block access systems or threaten to publish user data unless a ransom is paid.
- Theft of patient data: Stolen medical records can be used to conduct fraudulent activities, such as impersonating an individual in an attempt to receive reimbursement for healthcare services.
- Insider threats: Individuals who have access to key systems willingly or mistakenly put them at risk. Insider threats in healthcare can come from employees, former employees, or contractors/vendors.
- Hacked IoT devices: From security camera sensors to handheld medical devices, billions of devices are connected to each other thanks to the IoT. Hackers can take advantage of weak points in these connections to access systems with personal patient data.
Too many threats to healthcare cybersecurity exist to ignore the risks. In addition to acquiring personal patient data for financial gain, a security breach can cost lives. Strategies and practices to help prevent cyberattacks include the following:
- Cybersecurity training: Training staff in basic healthcare cybersecurity, such as never clicking on a link in an email from an unverified source, can play a big role in reducing cyber threats.
- Applying software updates promptly: Software updates typically include patches to address weak security, so ensure that systems have the latest software version.
- Implementing proven cybersecurity software: In addition to installing cybersecurity software on every connected machine, healthcare cybersecurity professionals can help address issues as they arise.
- Strengthening system access controls: Limiting access to those who need it can mitigate risk.
- Advocating best practices, such as updating passwords on all systems: Not only cybersecurity professionals are responsible for healthcare cybersecurity; everyone plays a role, even if simply updating passwords on a regular basis.
- Performing regular risk assessments: Risk/benefit assessments, especially for legacy systems, allow organizations to identify the weak points in a network.
Resources: Security strategies in healthcare
The following resources provide strategies and tips for reducing security breaches in healthcare:
- Digital Guardian, “Healthcare Cybersecurity: Tips for Securing Private Health Data”: Advice on developing a healthcare data protection program that goes beyond compliance.
- Healthcare IT News, “As Patient-Provider Experience Gets More Interconnected, New Security Strategies Needed”: Security strategies to make sure connected systems and data are properly safeguarded.
- HIMSS, “Cybersecurity in Healthcare”: Guide to healthcare cybersecurity outlining threats to look out for and discussing healthcare best practices, laws, and regulations.
- Security, “2021 Healthcare Cybersecurity Strategy: Start at the End”: Discussion on the role of endpoints — laptops, mobile devices, and workstations — in healthcare cybersecurity.
- Center for Internet Security, Cyber Attacks: In the Healthcare Sector: Different types of threats, with links to resources on mitigating the challenges.
- Healthcare IT News, “The Real Cybersecurity Risk Sits Between the Chair and Keyboard”: How human factors can improve cybersecurity shortcomings.
- HIMSS, “HIMSS Healthcare Cybersecurity Survey” and HIMSS, “2019 HIMSS Cybersecurity Survey”: Essential data highlighting the security threats to healthcare systems in the past two years.
Modernizing healthcare to reduce risk and improve care outcomes
The advantages of healthcare technology are clear. Technology enables:
- Physicians and other medical professionals to improve communication with their patients and other healthcare providers through smartphone apps, telehealth software, and texting
- Patients to be more proactive in their care thanks to digital health apps and patient portals that allow them to check on test results, schedule appointments, and renew subscriptions
- Healthcare facilities to improve operations, resulting in better care delivery, a more efficient workforce, and lower costs
Technology can also be a pain point if left unprotected. Modernization of healthcare systems enables organizations to adapt to digital trends and respond to patient preferences, but also reduce security risks by eliminating weak points hackers look to target.
By addressing the four cybersecurity challenges healthcare faces, namely patient privacy protection, legacy system vulnerabilities, IT challenges, and security breaches, healthcare organizations can improve quality of care and advance the industry. To succeed in this effort, they need to embrace health industry cybersecurity practices, understand the risks of inaction, and create a culture in which healthcare cybersecurity is a top priority.
Infographic Sources
Center for Internet Security, “Cyber Attacks: In the Healthcare Sector”
Center for Internet Security, “Insider Threats: In the Healthcare Sector”
CSO, “6 Biggest Healthcare Security Threats For 2020”
Healthcare IT News, “5 Cybersecurity Threats Healthcare Faces In 2019 And Beyond”
HealthTech, “How Healthcare Providers Can Safeguard Against Insider Misuse”
HealthTech Zone, “Impact of Technological Innovations in Healthcare”
HIT Infrastructure, “Dangers of Legacy Solutions to Health IT Infrastructure Systems”
Keysight Technologies, “Five IT Challenges Affecting the Healthcare Industry”
TechRepublic, “The 5 Biggest Cybersecurity Threats For The Healthcare Industry”

